The Russian Hacker Group Sandworm is Back: New Kapeka Malware Secretly Infecting Systems Since 2022
Novel malware recently found in Estonia links the Sandworm hacker group to cyberattacks in Europe, and may be a spillover from the Russia-Ukraine War.

What is Kapeka
Kapeka is a backdoor malware which is used in the initial stages of a cyberattack. It is used to allow an attacker to maintain cleverly hidden long-term access to victim's infrastructure in the event that they wish to make a return visit to siphon off new data or stage other attacks against an organization. What is interesting about Kapeka, compared to other types of malware is that it has been deployed somewhat sparingly and usually in specific targeted applications. Its threat also arises from the fact that it’s very well hidden in affected infrastructure, which makes it very difficult to defend against.
In a whitepaper detailing the ins and outs of Kapeka, threat researcher Mohammad Kazem Hassan Nejad explains:
"Kapeka contains a dropper that will drop and launch a backdoor on a victim's machine and then remove itself. The backdoor will first collect information and fingerprint both the machine and user before sending the details on to the threat actor. This allows tasks to be passed back to the machine or the backdoor’s configuration to be updated. WithSecure do not have insight as to how the Kapeka backdoor is propagated by Sandworm."
Kapeka was first discovered by Finnish security company WithSecure. The malware has been determined to be active in the wild since the middle of 2022 and its victims are by-and-large groups located in Eastern Europe. Through their analysis, WithSecure asserts that by linking the Kapeka malware to other kinds of ransomware attack they believe that this links the new malware to the well known APT hacker group Sandworm.
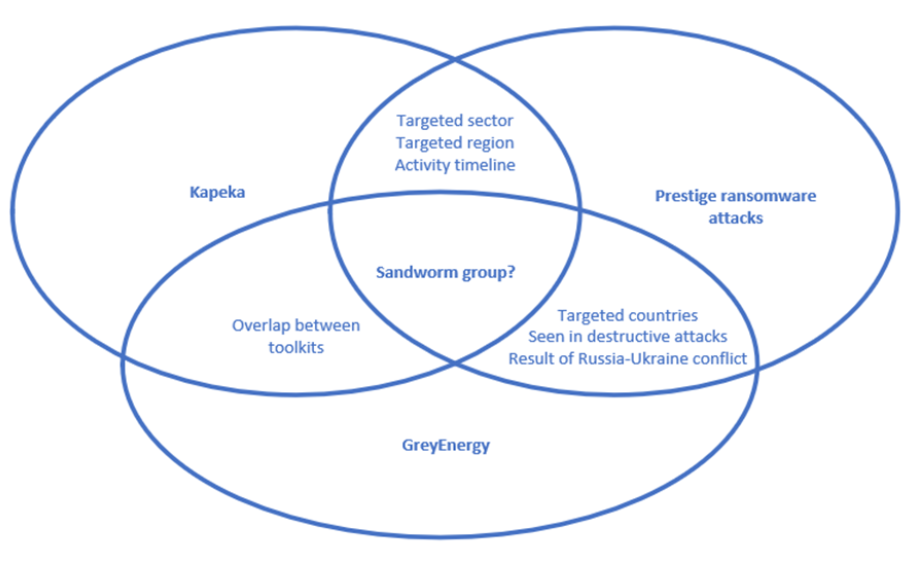
Sandworm attack attribution overlaps. (Image used with permission from WithSecure)
Who is Sandworm
Sandworm is a Russian government sponsored hacking group which is responsible for on-going attacks against Ukraine, which have even led to the spread of malware infections to other countries around the world. Sandworm first came to the attention of threat intelligence analysts at iSIGHT Partners uncovered a large spear-phishing campaign which was taking advantage of a zero-day vulnerability, now known as CVE-2014-4114.
This initial attack, after review by iSIGHT and Microsoft, determined that this attack was part of a Russian cyber-espionage campaign. They claimed in their blog post which explains the details of the attack that the following groups were visible targets of the Russian state-sponsored hack:
- NATO
- Ukrainian government
- Western European governments
- Polish energy companies
- European telecom companies
- US academic groups
Attributing the state behind such attacks can be difficult, the point of working through these sponsored groups is a layer of removal between a nation and the hackers themselves. iSIGHT concludes that the Russian government is ultimately behind the group because "many of the lures observed have been specific to the Ukrainian conflict with Russia and to broader geopolitical issues related to Russia."
Sandworm operates within Unit 74455 and is also known as the Main Center for Technologies within the Main Directorate of the General Staff of the Armed Forces of the Russian Federation. Sandworm is already known for lots of other attacks, and also goes by the names of BlackEnergy, Voodoo Bear, and Seashell Blizzard.
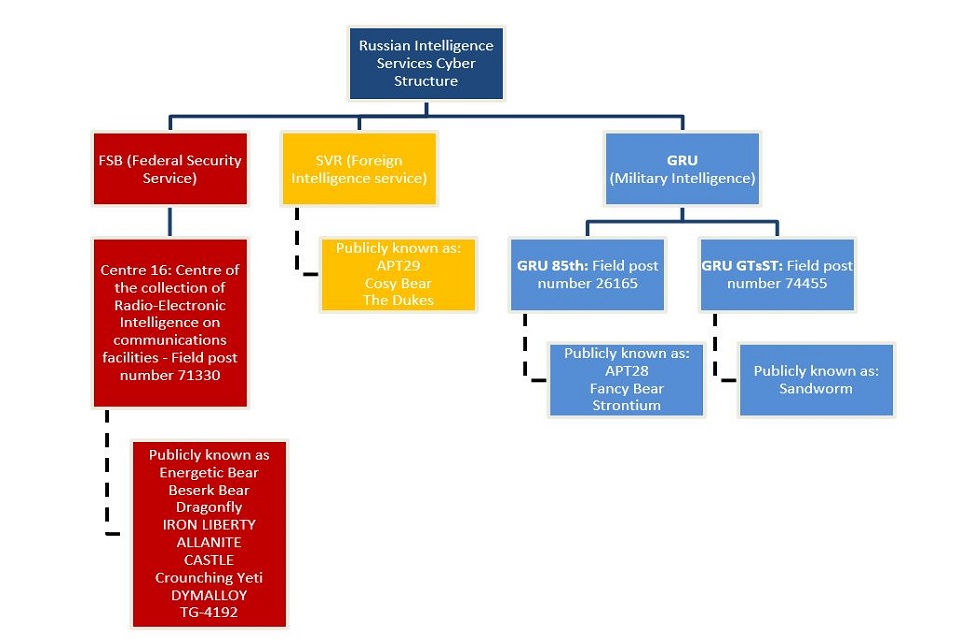
Both Sandworm and FancyBear are well known advanced persistent threats operating under the Russian GRU.
Attacks on Ukraine
Sandworm is best known for their attacks made against Ukraine. In the Winter of 2015 Sandworm attacked the power grid in the western part of Ukraine which led to around 230,000 customers experiencing major power outages during the frigid December temperatures. A similar attack hit Kyiv in December of 2016 leading to mass power outages and later reports showed that the intention was to physically damage critical electrical infrastructure.
They followed these attacks up in 2017 combining the EternalBlue exploit with NotPetya ransomware in a cyber attack which first hit Ukrainian infrastructure, banks, and gas stations. No computers with an internet connection were safe. The ransomware spread eventually hit global shipping company Maersk, at which point it spread around the world.
Threat to other European Nations
Sandworm is not only attacking Ukraine and more directed ransomware attacks will have a collateral effect on other countries. The 2017 NotPetya ransomware attacks are a perfect example of this. Since these attacks, Sandworm has also been deploying the Kapeka malware throughout countries in Eastern Europe since 2022. These countries are EU member states which are being attacked in the digital realm by a foreign adversary. WithSecure’s research suggests that "Kapeka's development and deployment likely follows the ongoing Russia-Ukraine conflict, with Kapeka being likely used in targeted attacks across Central and Eastern Europe..."
Google's Mandiant has also begun tracking Sandworm, titling them APT44. Their research has shown that Sandworm is behind a number of "hacktivist" groups operating through Telegram. The channels XakNet Team, CyberArmyofRussia_Reborn1, and Solntsepek have all been used by APT44 to take responsibility for their cyberattacks.
Mandiant concludes in their report that:
"Due to the group's history of aggressive use of network attack capabilities across political and military contexts, APT44 presents a persistent, high severity threat to governments and critical infrastructure operators globally where Russian national interests intersect."
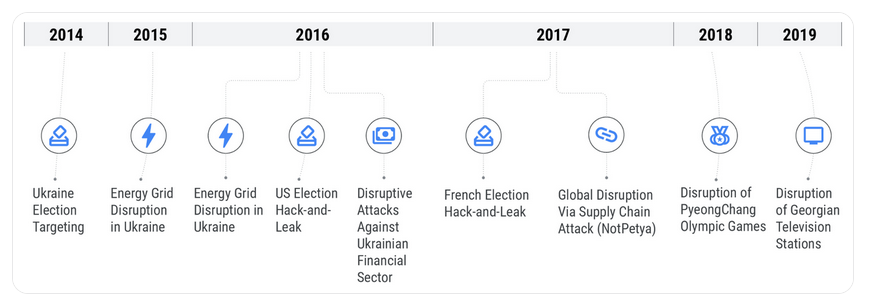
Timeline of Sandworm’s activities prior to the start of the Russia-Ukraine war. (Image used with permission from Mandiant)
As the EU and other nations around the world stand in support of Ukraine in the on-going conflict, the threat of cyberattacks from Sandworm must be taken seriously. Without being able to read the minds of APTs the best position we can take in protecting our businesses, government, and infrastructure systems is to take proper security steps beforehand. This is even more important when countries prepare to hold elections that will directly impact policies related to the Russia-Ukraine war.
Protecting your businesses and staying alert.
In their report, WithSecure includes a number of scripts and malware artifact details which can be used to detect Kapeka infections within your network. By keeping up with best recommended security practices and taking advantage of new threat intelligence research you can better keep your network and data safe against cyberattacks. Proper threat modeling is crucial to protecting your data and making sure that your network remains secure.
Attacks by malicious hackers like SandWorm show clearly why we must all work together to keep the internet as secure as possible. This includes fixing vulnerabilities quickly – and not keeping them open for backdoor access by own governments – as well as maintaining strong and unbreakable encryption for businesses and citizens alike.
Regular calls by politicians to undermine encryption like the EU Chat Control proposal or the US FISA reform go in the opposite direction: Such legislation destroys the security and confidentiality of the communication of every citizen.
Encryption is the best tool we have to protect our sensitive data from malicious attacks. Politicians must learn to uphold strong encryption for everybody’s security!
Stay safe out there and happy encrypting.