Cloudbleed Revealed Personal Information - And: What Is the Real Danger Behind a Service Like Cloudflare?

Every browser could see private data
The so called Cloudbleed bug is much worse than its little brother called Heartbleed as it not only affected millions of websites, in addition, it sent personal information like login data (even for banking websites) as well as private chat sessions from dating websites to any other browser accessing a website that uses Cloudflare.
Who has been a target?
The list of all affected websites is terribly long, so here are some important ones:
- authy.com
- coinbase.com
- bitpay.com
- news.ycombinator.com
- yelp.com
- okcupid.com
- uber.com
- localbitcoins.com
- zoho.com
- fitbit.com
- github.com
It is possible that you have recently visited one of these websites thinking you were safe as the lock for the SSL-connection was showing up green. But visiting these sites was like going to a cash machine to withdraw money. Everything seemed normal, except that the machine would still show all details of the previous user including his PIN and a copy of the used card, making it possible for you to withdraw money from his account. And it gets even worse: After you used this machine, your information might be shown to the next customer and so on and so forth.
Search engines made sensible information easily accessible
This information exchange was hidden within the browsers so it hugely went unnoticed. However, it is very likely that it was noticed by some. The traffic was cached automatically by search engines like Google and Bing, which made it easily accessible to anybody who accidentally found out about the leak, thus knowing what he was looking for. In addition, this information was visible to bots trawling the web so it might have already fallen into the hands of people with bad intentions.
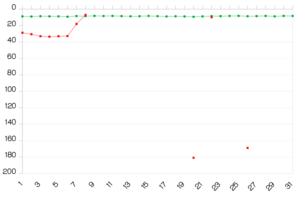
Google engineer Tavis Omady discovered the bug and it was fixed as well as search engine data scrubbed manually within a couple of days. However as the bug was probably active since September 2016, we advise you to change all passwords from affected websites. In addition if you are using your Tutanota password for anything else, please change it as well, just to be sure.
What information was leaked through Cloudbleed?
According to the official statement of Cloudflare, the problem was in the code of a new HTML parser, which suffered from a buffer overflow vulnerability triggered by unbalanced HTML tags on pages. The biggest amount of leakage took place between February 13 and February 18, which is also when Omady noticed the leakage.
Now imagine what malicious people with the leaked Cloudflare information can do: They can monitor the data flows of these websites - user names, passwords, communications, cookies and authentication tokens.
Why is it dangerous that Cloudflare has access to millions of SSL certificates?
Cloudflare is a service which protects websites from DDoS attacks. In order to be capable to protect HTTPS sessions, Cloudflare pretends to need access to the private keys of the SSL certificates of the "protected" websites, which by itself means that customers completely need to trust Cloudflare.
A SSL certificate gives you visual approval that you are currently viewing the website you intended to visit, and that it is safe to enter payment details and passwords.
Private keys of SSL certificates must never be trusted to third party services
If an attacker had a private key of an SSL certificate at his disposal, he could duplicate a website, let's say, of your bank, and you wouldn't even notice. He pretends that this is the original website, a classical Man-in-the-middle attack. Now you want to transfer money online and go to your bank's website. You check whether the connection is secure, because you are a prudent person. Everything seems to be alright, so you enter your credit card details and hit the send button.
And now? Your payment details are sent directly to the attacker - you did not visit your bank's website as you thought, you have just been to the malicious duplicate. Fortunately, this is not what happened with Cloudbleed, but this is exactly the reason why we at Tutanota would never use Cloudflare or any similar service.
In a nutshell, the real danger of any service like Cloudflare is that they collect the private keys of millions of SSL certificates, which makes them an extremely attractive target not only for attackers, but also for secret services. With the private keys, the NSA would be able to decrypt everything - yes, every little bit of data you generated through these affected websites.
Our advice to you
Change your passwords. The people in charge may communicate that the data has disappeared from the internet now, but no-one knows who already had access to the data. For instance, no-one knows whether Omady was the first or the only one to notice this data leakage. Even if your information has not been leaked, it is always a good idea to change your passwords every once in a while.
Your secure mails in Tutanota are not affected
As Tutanota does not use Cloudlfare - we would never hand the private keys of our SSL certificates to anyone - you can be sure that your secure mailbox is not affected.
In case you were using the same passwords for Tutanota and other services, please also change your Tutanota password. And make it unique - plus write it down somewhere safe as we cannot reset it.
Although attackers may have recorded a lot of your online traffic, we have good news for you: Your data in Tutanota is encrypted. Your Tutanota emails are not accessible to anyone apart from yourself.

No comments available